Demystifying AWS VPC
Rohit K.
July 4, 2025
When building on the cloud, one of the foundational components you’ll encounter is the Virtual Private Cloud (VPC). Whether you’re launching a basic web application or architecting a multi-tier enterprise system, understanding VPCs is essential — not just for connectivity, but for security, cost efficiency, and compliance.
In this blog, we’ll explore the importance of AWS VPC, especially from a security perspective, and compare the cost and use cases of public vs. private subnets. We’ll also touch on best practices and common architecture patterns to get the most out of your VPC.
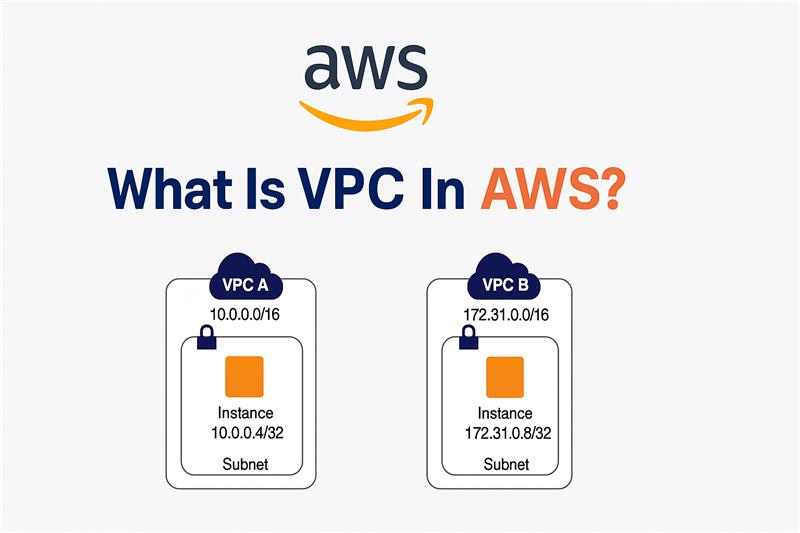
What Is a VPC in AWS?
A VPC (Virtual Private Cloud) is your isolated network environment within AWS. Think of it like a data center carved out for you in the cloud. You define the IP range, create subnets, configure routing tables, and control access using security groups and network ACLs.
It allows you to:
- Launch EC2 instances in logically isolated networks
- Control inbound and outbound traffic at multiple levels
- Connect securely to on-premise environments using VPN or AWS Direct Connect
- Segment your environment using public and private subnets
Why VPC Is Critical for Security
In a cloud-first world, security is everything. AWS VPC helps enforce defense-in-depth architecture. Here’s how:
1. Isolation
Each VPC is isolated from others, meaning no cross-traffic unless explicitly allowed via peering or Transit Gateway.
2. Security Groups & NACLs
These act as virtual firewalls. Security groups work at the instance level, while network ACLs function at the subnet level, allowing granular traffic control.
3. Private Subnets
Resources like databases or backend services should never be publicly accessible. Using private subnets ensures they’re shielded from the internet while still being accessible internally.
4. Flow Logs
You can monitor network traffic and detect suspicious behavior using VPC Flow Logs — useful for audits, security investigations, and anomaly detection.
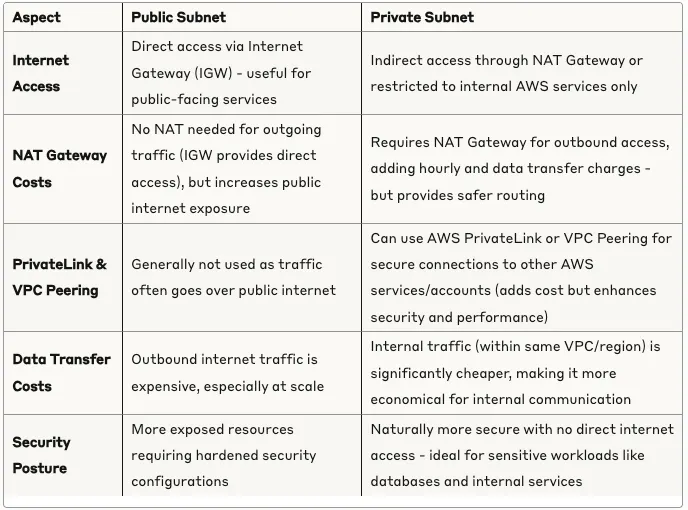
Cost Considerations: Public vs. Private Networking
When architecting your AWS infrastructure, understanding the cost dynamics between public and private subnets is crucial. Here’s how they differ:
Real-World Use Cases
Here are a few common patterns where VPC design plays a key role:
Web Application with DB
- Public Subnet: Load Balancer, EC2 frontend
- Private Subnet: RDS, ElastiCache, backend services
Serverless + Private APIs
Use VPC endpoints to securely connect AWS Lambda functions to services like DynamoDB or S3 — without exposing traffic to the internet.
Hybrid Cloud
Connect your AWS VPC to your on-premise infrastructure via VPN or AWS Direct Connect for a secure hybrid model.
Best Practices for VPC Architecture
To make the most of your VPC setup, keep these practices in mind:
- Use multiple Availability Zones (AZs) for high availability and fault tolerance.
- Place sensitive components like databases in private subnets.
- Enable VPC Flow Logs to monitor traffic and support auditing.
- Limit access with tight security group and NACL rules.
- Use Systems Manager (SSM) for remote access instead of exposing instances via SSH.
Final Thoughts
Your VPC is more than just a network layer — it’s the foundation of your cloud security and architecture. A well-architected VPC not only improves your system’s security posture, but also helps optimize costs and performance.
Whether you’re deploying a startup MVP or scaling an enterprise application, don’t overlook your VPC strategy. Secure by design is always better than patching later.
Build smart. Build secure. Start with your VPC.
