Why Encrypting and Decrypting Data Is Essential for App and Backend Security
Jaydip K.
Jan 01, 2026

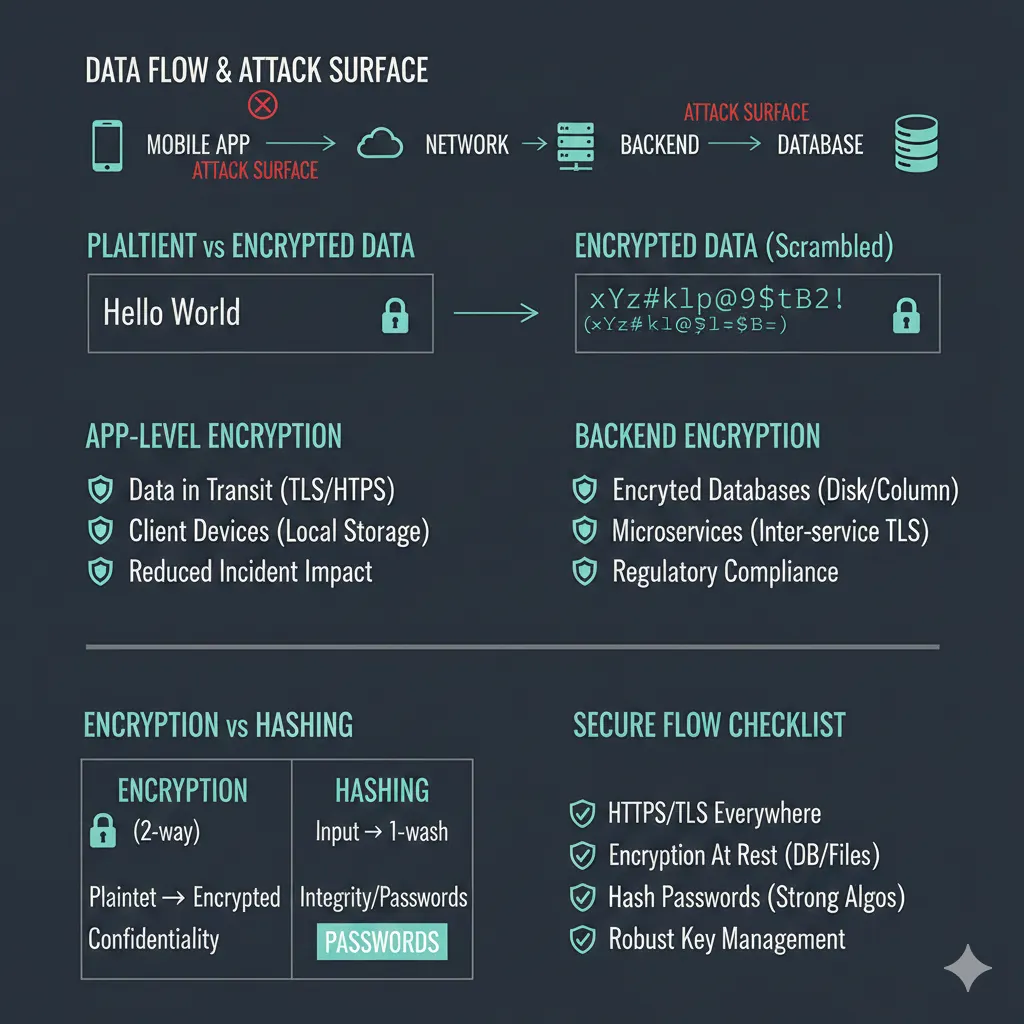
Modern applications handle sensitive information by default — user credentials, personal details, access tokens, and payment data. This data constantly moves between client applications (web or mobile), backend services, and databases.
The risk isn’t hypothetical. Any point in that flow — network transit, local storage, logs, or databases — can become an attack surface. Without encryption, a single interception or breach can expose data in plain text.
This is why encryption and decryption are not “advanced security features.” They are baseline requirements for building systems that can safely operate at scale.
Encryption and Decryption: The Practical View
At a high level:
- Encryption transforms readable data (plaintext) into an unreadable format (ciphertext) using an algorithm and a secret key.
- Decryption reverses that process, restoring the original data only for authorized systems that possess the correct key.
Conceptually:
Plaintext → Encrypted Data → Plaintext
The critical idea is separation: data without keys is useless. Even if encrypted data is exposed, it cannot be meaningfully exploited unless the attacker also gains access to the key material.
Why Encryption Matters at the Application Layer
1. Data in Transit Is Always at Risk
Applications frequently operate over networks you don’t control — public Wi-Fi, mobile carriers, proxies, or shared infrastructure. Encryption ensures that intercepted traffic cannot be read or altered in transit.
This is why HTTPS/TLS is table stakes, and why additional payload-level encryption is sometimes required for highly sensitive data.
2. Client Devices Are Not Trusted Environments
Browsers and mobile devices cache data, store tokens, and persist state. If a device is compromised, unencrypted data becomes immediately accessible. Encrypting sensitive client-side data limits the damage of lost, stolen, or rooted devices.
3. Encryption Reduces Incident Impact
From a business perspective, encryption doesn’t just prevent attacks — it reduces blast radius. When exposed data is encrypted, incidents are easier to contain, disclose, and recover from.
Why Backend Systems Depend on Encryption
1. Breaches Happen — Design for That Reality
No system is immune to compromise. Encrypting sensitive database fields ensures that a database breach does not automatically become a data breach.
2. Controlled Access Inside Distributed Systems
Modern backends consist of multiple services. Encryption allows only explicitly authorized services to decrypt sensitive fields, even if they can query the same database.
3. Regulatory and Contractual Requirements
Security standards and compliance frameworks increasingly assume encryption for sensitive data both at rest and in transit. Encryption is often the difference between a reportable incident and a contained event.
A Practical Example: Encrypting and Decrypting Data in Python (AES)
For application-level data (tokens, secrets, PII), symmetric encryption is commonly used due to its performance and simplicity.
Install the Dependency
pip install cryptography
Encrypting Data
from cryptography.fernet import Fernet
# Generate a secret key (store securely, never hardcode in production)
key = Fernet.generate_key()
cipher = Fernet(key)
data = b"SensitiveUserData"
encrypted_data = cipher.encrypt(data)
print("Encrypted Data:", encrypted_data)
Decrypting Data
decrypted_data = cipher.decrypt(encrypted_data)
print("Decrypted Data:", decrypted_data.decode())
This pattern is typically used for:
- Encrypting sensitive fields before database storage
- Protecting tokens exchanged between services
- Securing secrets that must be retrievable at runtime
The encryption itself is only half the solution — key storage, rotation, and access control are equally important.
A Critical Distinction: Passwords Must Not Be Encrypted
One of the most common and dangerous mistakes in application security is treating passwords like other sensitive data.
Passwords should never be encrypted and decrypted.
If a system can decrypt a password, it is already unsafe by design.
Correct Approach: Password Hashing (bcrypt)
import bcrypt
password = b"MySecurePassword"
hashed_password = bcrypt.hashpw(password, bcrypt.gensalt())
is_valid = bcrypt.checkpw(password, hashed_password)
print("Hashed Password:", hashed_password)
print("Password Valid:", is_valid)
Hashing is one-way. Even if a password database is leaked, original passwords cannot be recovered — only verified.
A Realistic App-to-Backend Security Flow
In well-designed systems, secure data handling typically follows this flow:
- Client apps send sensitive data over HTTPS (and encrypt payloads when needed)
- Backends decrypt data only for explicit use cases
- Sensitive database fields are encrypted at rest
- Passwords are stored exclusively as hashes
- Encryption keys are isolated using environment variables, KMS solutions, or vaults
This layered approach ensures no single failure exposes everything.
What This Means for Developers and Decision-Makers
- Encryption protects data even when systems fail
- Hashing is mandatory for credentials
- Algorithms matter, but operational discipline matters more
- MD5 is not encryption and should never be used for security
- AES is well-suited for sensitive application data
- bcrypt or Argon2 are the correct tools for passwords
Final Thought
Encryption and decryption are not about achieving perfect security — they’re about controlling damage when something goes wrong.
Systems that treat encryption as a default, not an afterthought, are easier to operate, safer to scale, and more resilient under pressure. Whether you’re writing code, reviewing architecture, or approving risk decisions, encryption is one of the simplest ways to make failure survivable.
